MEET THE MET 6 EDGE PREP MACHINE
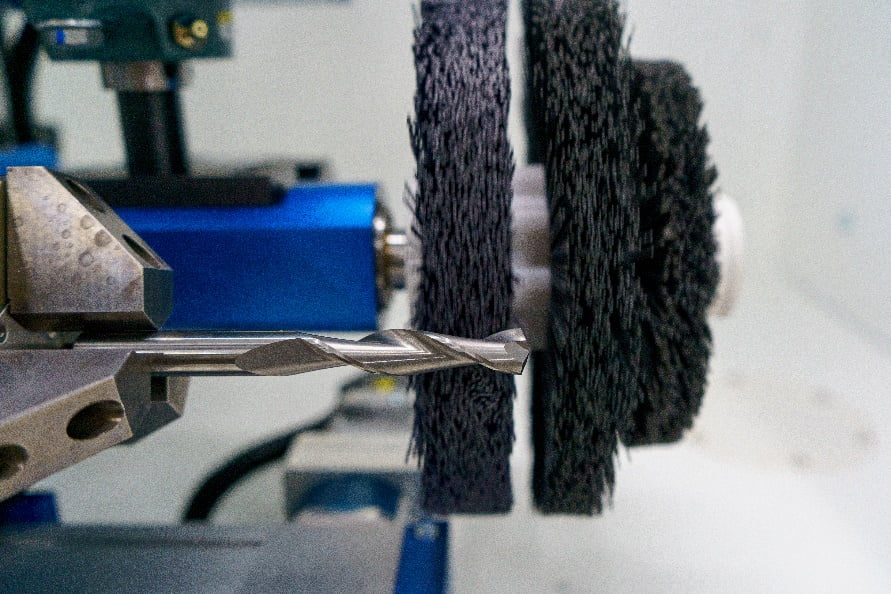
MEET THE MET 6 EDGE PREP MACHINE
MET offers existing machines and processes to meet your needs, or we can create custom solutions for your unique project
Why Choose MET?
We're Edge Prep Experts
We’re not jacks of all trades. We are a master of one. We’re not a machining company or an automation company that happens to offer edge prep systems. We’re an edge prep technology company first. There’s a difference, and you’ll see it in our solutions.
Schedule Your Sample Edge Prep Test
Do you want to improve the performance of your cutting tools? We can take the mystery out of the edge prep process and test directly on our equipment. Our team offers a no-charge application evaluation with a detailed application report and process description, so you can see our customer support firsthand and, most importantly, the excellence, precision, and quality of our edge prep capabilities.
Fast Customer Support
There is a common thread throughout our long history: a commitment to exceptional customer support. Your success means our success, and that’s why our goal is long-term partnerships. Our team is along for the ride with you and is available throughout the process of sample testing and solution building, all the way to maintenance.For MET, we provide the highest levels of attentiveness and follow-through, expertise, and speed. You should expect nothing less.